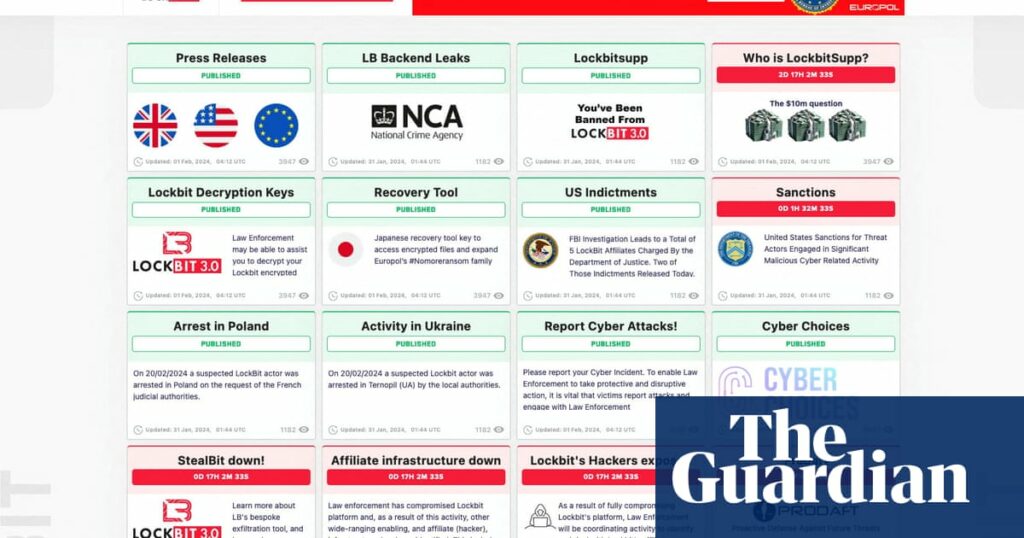
The LockBit ransomware gang is re-emerging, following a recent international crackdown that severely disrupted its operations.
Based in Russia, the group has created new dark web sites to showcase a few alleged victims and release stolen data. The gang is now under investigation by the National Crime Agency in Britain, as well as the FBI and other law enforcement agencies. This comes after a joint operation led by Europol to target the group last week.
In a statement issued in English and Russian, LockBitSupp, the group’s administrator, claimed that law enforcement agencies hacked their previous dark web site by exploiting vulnerabilities in PHP, a commonly used programming language for websites. They assured that other servers with backup blogs not using PHP would continue leaking data from targeted companies.
The statement also mentioned personal negligence and irresponsibility, along with expressing support for Donald Trump in the U.S. presidential election. The group even offered a job to the individual who hacked their main site. Law enforcement confirmed that LockBitSupp does not reside in the U.S. and is cooperating with authorities.
Despite the disruption, the NCA stated that LockBit remains compromised, but they are vigilant as the group may attempt to reorganize. Additionally, the U.S. has indicted two Russians for deploying LockBit ransomware globally. Ukrainian police also arrested suspects related to attacks carried out using LockBit’s malicious software.
The renewed Rockbit website has issued threats against U.S. government sites and listed more alleged hacking victims. Security experts indicate that the group is attempting to resume operations but will face challenges due to the damage caused by international law enforcement actions.
LockBit operates on a ransomware-as-a-service model, leasing software to criminal organizations in exchange for a cut of the ransom payments. Despite the setback, the group needs to rebuild its reputation within the criminal community to attract affiliates following the recent law enforcement activities.
Ransomware attacks involve hackers infiltrating a target’s system, disabling it with malware, and encrypting files for ransom. Recent trends include extracting sensitive data like personal and customer information and demanding payment in cryptocurrency, mainly Bitcoin, to decrypt files or delete stolen data copies. Last year saw a record $1.1 billion paid in ransomware payments.
Source: www.theguardian.com